Operate your business in Cloud with AsiaNet
Not all clouds are the same and not one type of cloud computing service is right for every enterprise. AsiaNet provides cloud services for businesses of all service providers and enterprises. The service allows you to run applications and remotely monitor your business through the internet. Cloud computing can be intimidating to understand, set up, and implement; but with the help of AsiaNet, this process is quick, flexible, and easy!
Cloud DDoS Protection
Launching DDoS attacks has never been easier. The technical barrier has mostly been removed due to the commoditization of DDoS tools and the emergence of DDoS-as-a-Service tools which enable sophisticated multi-vector attacks on both the network and application layer. The attacks can adapt quickly and require an immediate response. When an attack grows volumetric, no matter what on-premise equipment exists, a diversion to cloud scrubbing is required in order to absorb and mitigate the attack. Cloud DDoS Protection Services provide enterprise-grade DDoS protection in the cloud and delivers the most accurate detection and shortest time to protection from today’s most dynamic and constantly evolving DDoS threats, including SSL-based attacks.
Cloud DDoS Protection Services provide enterprise-grade DDoS protection
DDoS protection in the cloud and delivers the most accurate detection and shortest time
Most dynamic and constantly evolving DDoS threats, including SSL-based attacks.


COMPREHENSIVE PROTECTION
COVERAGE AGAINST OWASP
TOP 10 THREATS AND OTHER VULNERABILITIES.


Cloud WAF
Web application development is becoming more complex, rapid and more vulnerable than ever before. The Cloud WAF Service provides the web application security by using a positive security model based on machine-learning technologies to provide comprehensive protection coverage against OWASP Top 10 threats and other vulnerabilities. The Cloud WAF Service provides dynamic security policies with automatic false-positive correction, built-in DDoS protection, integrated bot mitigation and many other features to help protect organizations against the risk of data loss.

Automatic false-positive correction, built-in DDoS protection
Help protect organizations against the risk of data loss.

Using a positive security model based on machine-learning technologies
Competitors and adversaries alike often deploy
“bad” bots that leverage different methods to achieve nefarious objectives.
Cloud Bot Manager
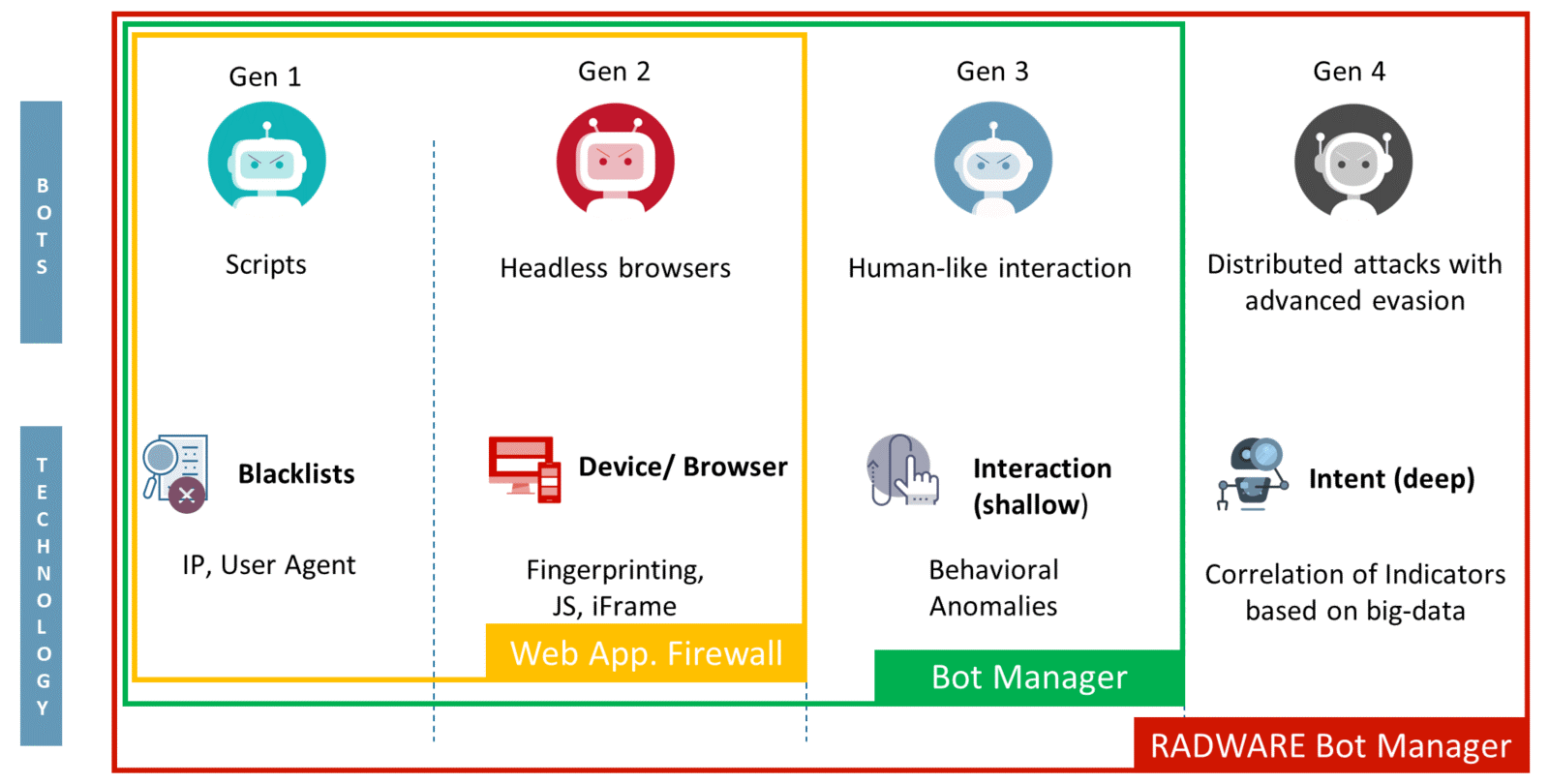
Over half of all internet traffic is generated by bots – some legitimate, some malicious. Competitors and adversaries alike often deploy “bad” bots that leverage different methods to achieve nefarious objectives. This includes account takeover, scraping data, denying available inventory and launching denial-of-service (DoS) attacks with the intent of stealing data or causing service disruptions. Leveraging proprietary, semi-supervised machine learning capabilities, Bot Manager allows precise bot management across web and mobile applications and application programming interfaces (APIs), combining behavioral modeling for granular intent analysis, collective bot intelligence and device fingerprinting.
Bot Manager Provide protection from a wide array of threats including:
- Account Takeover
- Gift Card Fraud
- Application DDos
- Price/Content Scrapping
- Digital Ad Fraud
- Skewed Analytics
- Form Spam

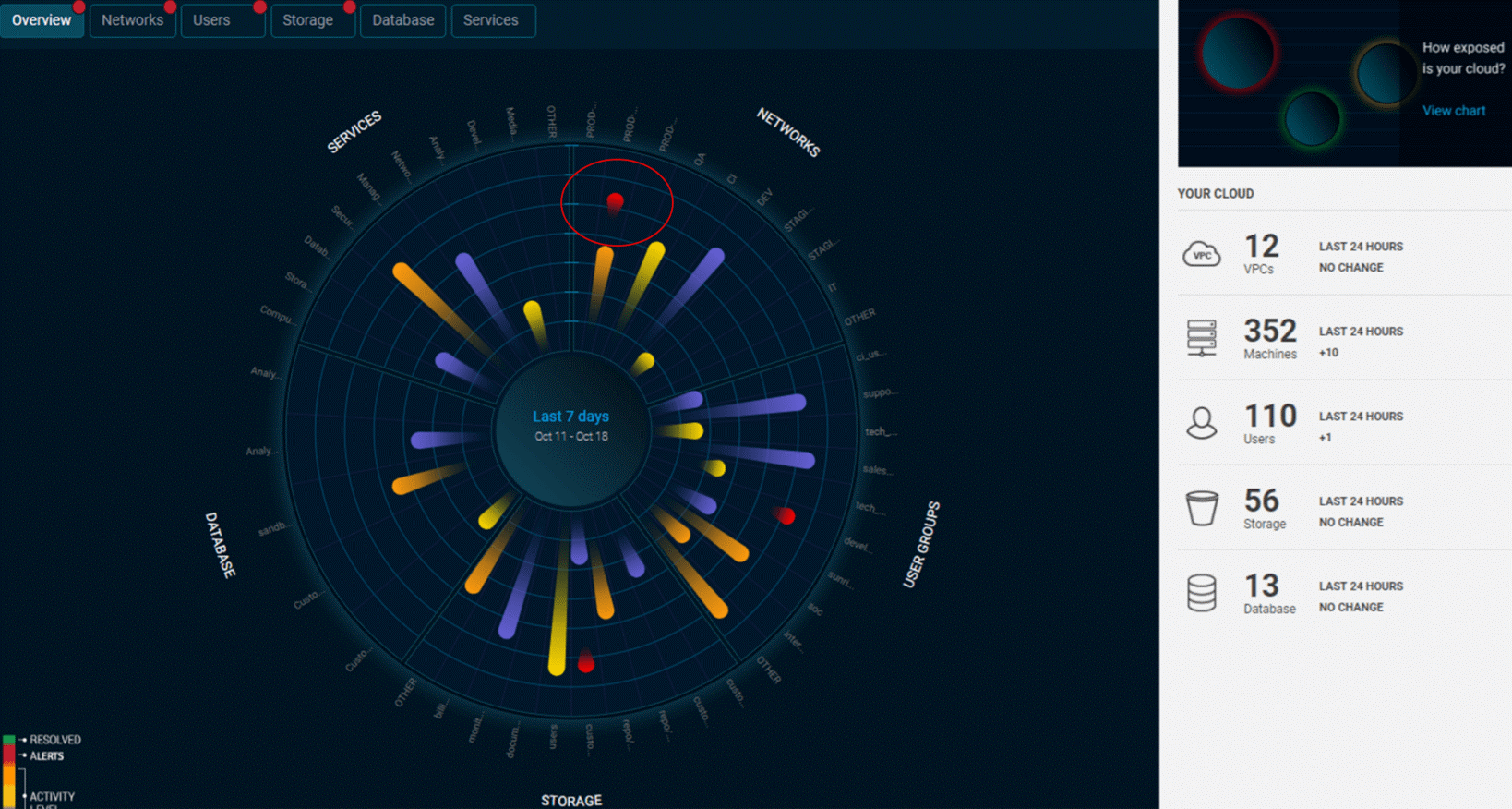
Cloud Workload Protection
Transitioning to the cloud means losing visibility and control over computing assets. Cloud-hosted workloads are managed remotely, making it difficult for security teams to supervise access to sensitive cloud resources. As a result, many organizations are unable to prevent cloud misconfigurations, identify cyberattacks as they are happening and respond in time.It’s time to take a different approach to workload defense!


Cloud Deception
Deception becomes deterministic by publicizing decoys with breadcrumbs on real assets luring attackers, malicious insiders, and automated malware to the decoys. Instead of searching in vain for the bad actor within an ocean of good data, deception delivers actionable alerts and events from decoys, AD credentials, poisoned data, and traffic analysis. These alerts have extremely high fidelity. Using deception on-premises and cloud with fresh activity data creates persuasive deception layers that include devices, data, and behavior all designed to turn the tables on attackers. They pursue the lures to decoys so you can detect and defend. Cloud VM Deception solution provides real OS or emulation decoys for hybrid environments. Use deception as a smart alarm system to detect post-breach attacks or learn about TTPs.
